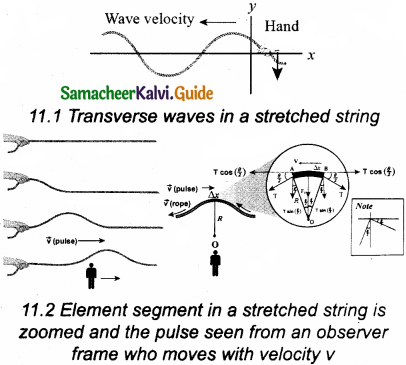
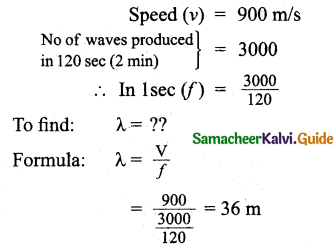
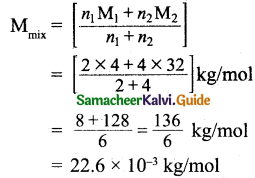
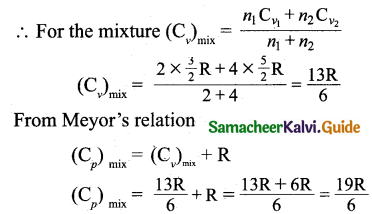
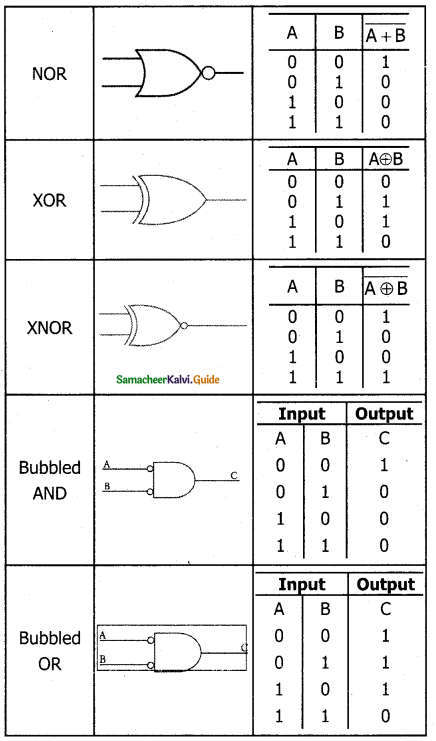
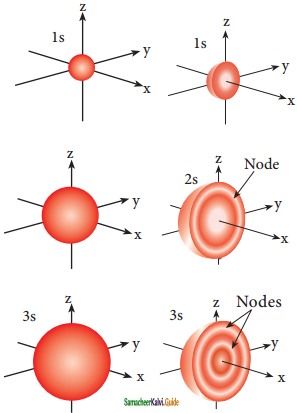
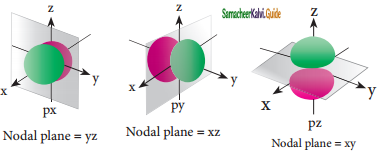
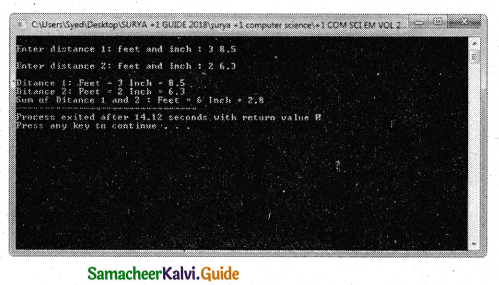
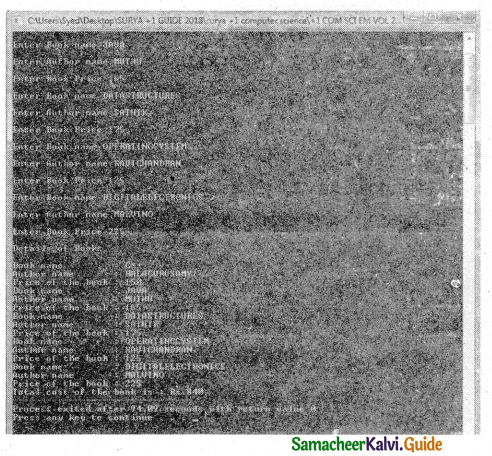
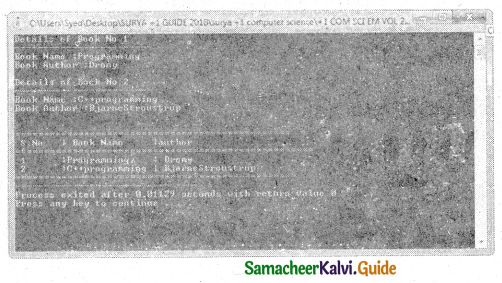
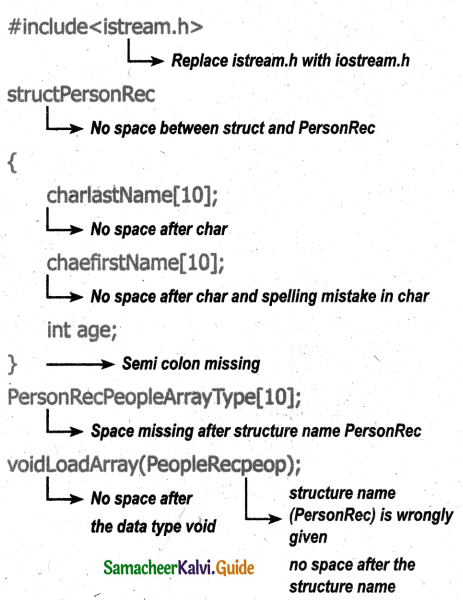
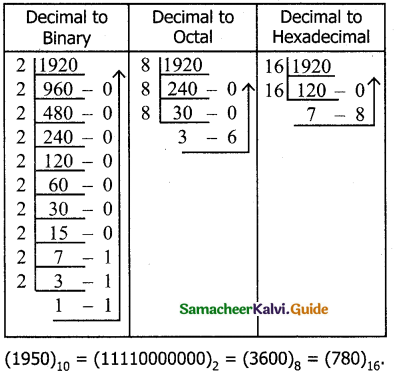
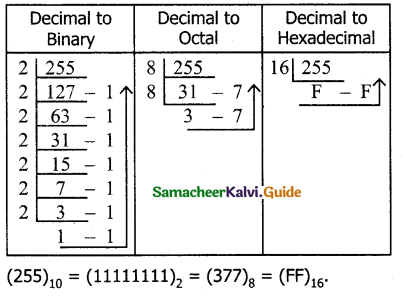
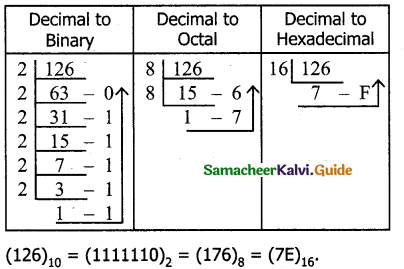
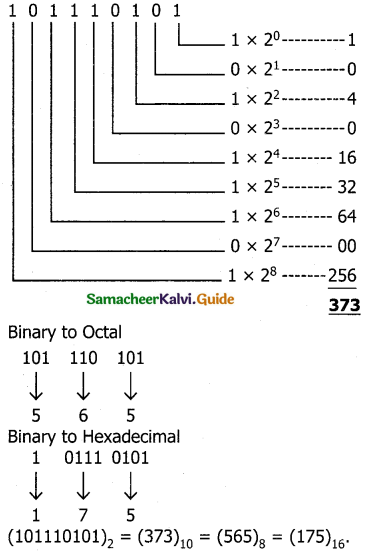
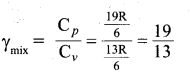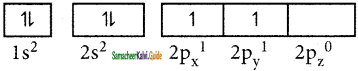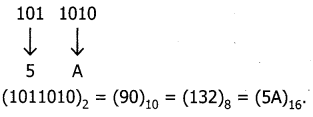Tamilnadu State Board New Syllabus Samacheer Kalvi 11th Bio Botany Guide Pdf Chapter 7 Cell Cycle Text Book Back Questions and Answers, Notes.
Tamilnadu Samacheer Kalvi 11th Bio Botany Solutions Chapter 7 Cell Cycle
11th Bio Botany Guide Cell Cycle Text Book Back Questions and Answers
Choose The Correct Answer:
Question 1.
The correct sequence in cell cycle is
a) S M G1 G2
b) S G1 G2 M
c) G1 S G2 M
d) M G1 G2 S
Answer:
c) G1 S G2 M
Question 2.
If mitotic division is restricted in G, phase the cell cycle, then the condition is known as
a) S Phase
b) G2 Phase
c) M Phase
d) G0 phase
Answer:
d) G0 phase
![]()
Question 3.
Anaphase promoting complex APC is a protein degradation machinery necessary for proper mitosis of animal cells. If APC is defective in a human cells. Which of the following is expected to occur?
a) Chromosomes will be fragmented
b) Chromosomes will not condense
c) Chromosomes will not regregate
d) Recombination of Chromosomes will occur
Answer:
c) Chromosomes will not segregate
Question 4.
In the S phase of cell cycle
a) Amount of DNA doubles in each cell
b) Amount of DNA remain same in each cell
c) Chromosome number is increased
d) Amount of DNA is reduced to half in each cell
Answer:
a) Amount of DNA doubles in each cell
![]()
Question 5.
The centromere is required for
a) Transcription
b) Crossing over
c) Cytoplasmic cleavage
d) movement of chromosome towards the pole
Answer:
d) movement of chromosome towards the pole
Question 6.
Synapsis occurs between
a) m RNA and ribosomes
b) spindle fibres and centromeres
c) two homologous chromosomes
d) a male and a female gemale
Answer:
c) two homologous chromosomes
![]()
Question 7.
In meiosis crossing over is initiated at
a) Diplotene
b) Pachytene
c) Leptotene
d) Zygotene
Answer:
b) Pachytene
Question 8.
Colchicine prevents the mitosis of the cells at which of the following stage
a) Anaphase
b) Metaphase
c) Prophase
d) Interphase
Answer:
a) Anaphase
![]()
Question 9.
The pairing of homologous chromosomes on meiosis is known as
a) Bivalent
b) Synapsis
c) Disjunction
d) Synergids
Answer:
b) Synapsis
Question 10.
Anastral mitosis is the characteristic feature of
a) Lower animals
b) Higher animals
c) Higher plants
d) All living Organism
Answer:
c) Higher plants
![]()
Question 11.
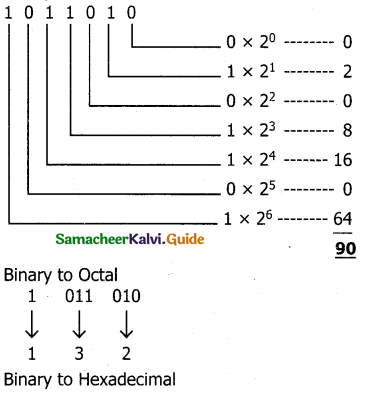
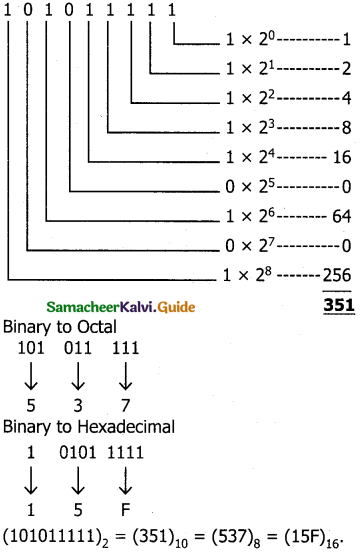
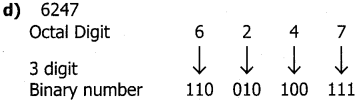
Write any three significance of mitosis
Answer:
Exact copy of the parent cell is produced by mitosis (genetically identical).
- Genetic stability – daughter cells are genetically identical to parent cells.
- Repair of tissues – damaged cells must be replaced by identical new cells by mitosis.
- Regeneration – Arms of starfish.
Question 12.
Differentiate between Mitosis and Meiosis.
Answer:
Differences between Mitosis and Meiosis
|
Mitosis |
Meiosis |
| One division | Two division |
| The number of chromosomes remains the same | The number of chromosomes is halved |
| Homologous chromosomes line up separately on the metaphase plate | Homologous chromosomes line up in pairs at the metaphase plate |
| Homologous chromosome do not pair up | Homologous chromosome pair up to form bivalent |
| Chiasmata do not form and crossing over never occurs | Chiasmata form and crossing over occurs |
| Daughter cells are genetically identical | Daughter cells are genetically different from the parent cells |
| Two daughter cells are formed | Four daughter cells are formed |
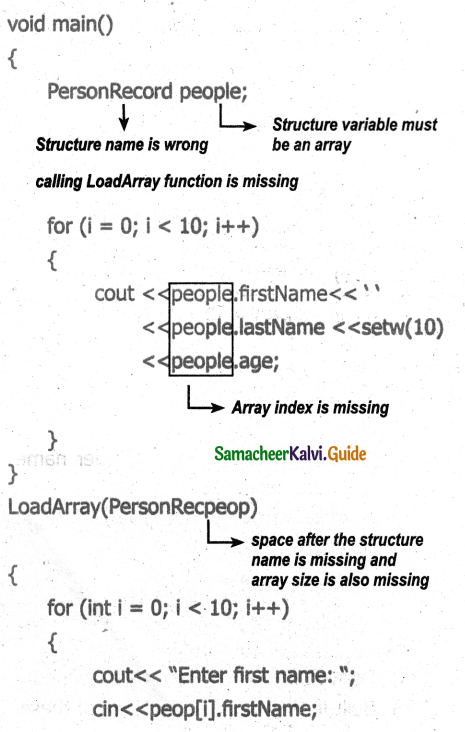
Question 13.
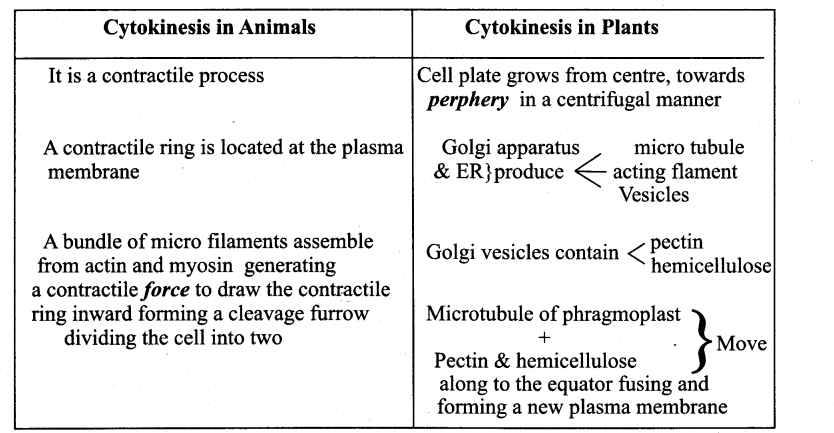
Differentiate Cytokinesis in plant cells & animal cells
Answer:

Question 14.
Given an account of the Go phase.
Answer:
Some cells exit G1 and enters a quiescent stage called G0, where the cells remain metabolically active without proliferation. Cells can exist for long periods in G0 phase. In G0 cells cease growth with reduced rate of RNA and protein synthesis. The G0 phase is not permanent. Mature neuron and skeletal muscle cell remain permanently in G0. Many cells in animals remains in G0 unless called onto proliferate by appropriate growth factors or other extracellular signals. G0 cells are not dormant.
![]()
Question 15.
Write about the Pachytene and Diplotene stage of Prophase I.
Answer:
3. Pachytene stage
- Chromosome appear as bivalent or tetrads
- 4 chromatids & 2 centromeres are seen
- Synapsis of homologous chromosomes between non-sister chromatids completes except at chiasmata where crossing over occurs
- Recombination (exchange of chromosomal bits is completed by the end) – but chromosomes are linked at the sites of crossing over
- Enzyme – Recombinase mediates the process.
![]()
4. Diplotene
- Synaptonemal complex disassembled & dissolves
- Nonsister chromatids of homologous chromosomes get attached where x like shape occur at Crossing over known as chiasmata holding the homologous chromosomes together the homologous chromosomes tend to separate except at chiasmat
- The sub-stage last for days or years depending on the sex & the organism follows Pachytene
- synaptical complex disassembled & dissolves
- The chromosomes are actively transcribed in females as the eggs stores up materials for embryonic development
- Exception In Lamp brush chromosome prominent loops occur.
11th Bio Botany Guide Cell Cycle Additional Important Questions and Answers
I.Choose the correct answer: (1 Marks)
Question 1.
Most of the neurons in the brain are in …………… stage.
(a) G1
(b) S
(c) G2
(d) G0
Answer:
(d) G0
Question 2.
Un differentiated cells include
a) Stem cells in animals
b) Meristematic cells in plants
c) RBC which carry out the transportation of oxygen
d) Mesophyll cells which carry out photosynthesis
(i) a & b
(ii) c & d
(iii) a & c
(iv) b & c
Answer:
(i) a & b
![]()
Question 3.
Robert Brown discovered the nucleus in the cells of …………… roots.
(a) Mirabilis
(b) Orchid
(c) Moringa
(d) Oryza
Answer:
(b) Orchid
Question 4.
The proteins that activate the cell to perform cell division are
a) Actin and Myosin
b) Kinases and Cyclin
c) Histamine and Cyclin
d) Tubulin and Actin
Answer:
b) Kinases & Cyclin
![]()
Question 5.
The number of chromosomes in the onion cell is …………….
(a) 8
(b) 16
(c) 32
(d) 64
Answer:
(a) 16
Question 6.
Mitosis is called
a) Direct cell division
b) Indirect cell division
c) Mitotic Meiotic cell division
d) Reduction division
Answer:
a) Direct cell division
![]()
Question 7.
During Anaphase
(I) The daughter chromosome move to the opposite poles due to the shortening of the phragmoplast
(II) due to the thickening of chromosomes
(III) Shortening of microtubules
(IV) Shortening of asters
Answer:
(III) Shortening of microtubules
Question 8.
Cell cycle was discovered by …………….
(a) Singer & Nicolson
(b) Prevost & Dumans
(c) Schleider & Schwann
(d) Boveri
Answer:
(b) Prevost & Dumans
![]()
Question 9.
The cells without nucleus are
a) RBC – platelets, tracheids & vessels
b) RBC – sievetube, companion cells thrombocytes
c) WBC – platelets, companion cells & vessels
d) RBC – platelets, companion cells & neurons
Answer:
a) RBC – platelets, tracheids & vessels
Question 10.
The stage between two meiotic division is called
a) Cytokinesis
b) Interphase I
c) Inter kinesis
d) Interphase II
Answer:
c) Inter kinesis
![]()
Question 11.
Replication of DNA occurs at …………… phase.
(a) G0
(b) G1
(c) S
(d) G2
Answer:
(c) S
II. Find out the true and false statements from the following and on that basis find the correct answer.
Question 1.
(I) Nucleolus disappear during the metaphase stage of mitosis
(II) The microtubules arrange to form asters in plant cells
(III) In plant cells phragmoplast is formed prior to the formation of cell plate
(IV) Mitosis is responsible for the Regeneration of lost arms of starfish
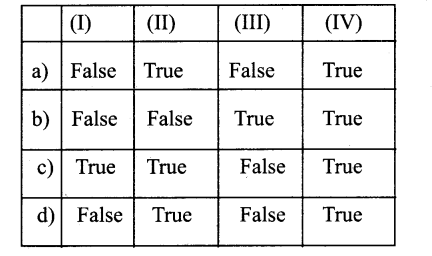
Answer:
b) False – False – True- True
![]()
Question 2.
(i) The word Protoplasm was coined by – Purkinje
(ii) Structure of bacteria was observed first – Edouard Van Beneden through a microscope by
(iii) Centrosome & Chromosome theory – Theodor Boveri Proposed by
(iv) Cell division in round Worm was – Walther Flemming Observed by
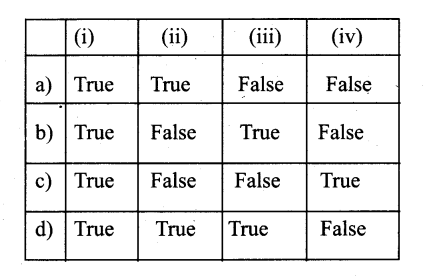
Answer:
b) True – False – True – False
Question 3.
(i) C Value is the amount in picograms of DNA contained within a haploid Nucleus
(ii) Nucleolan membrane disappear during Ana Phase stage of mitosis
(iii) The arrangement of microtubules is called to form Asters -, which is a unique feature of plant cells
(iv) One of the protein synthesis in G2 – phase is known as Maturation Promoting Factor
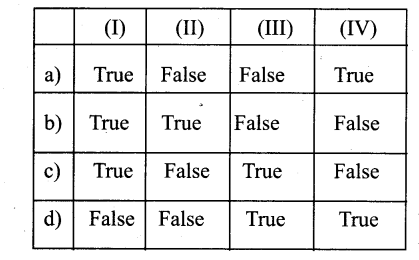
Answer:
a) True – False – False – True
![]()
III. Find out the correct match from the following.
Question 1.
Zygotene – Chromosomes appear as tetrads
Pachytene – Synapsis of homologous chromosomes occur
Diplotene – Condensation of chromosomes takes place
Diakinesis – Terminalisation of chiasmata occur & Nucleolus Disappear
Answer:
Diakinesis -Terminalisation of chiasmata occur & Nucleolus Disappear
Question 2.
Duration of different Phases of cell cycle given find out the correct match
(I) S Phase – 12 Hours
(II) G1 Phase – 11 Hours
(III) G2 Phase – 4 Hours
(IV) M Phase – 2 Hours
Answer:
(III) G2 Phase – 4 Hours
IV. Find out the Wrong match
Question 1.
(I) The chromosome does not divide as chromatids, for centromere does not divide – Anaphase I
(II) The chromatids move to the opposite poles by the splitting of the centromere – Anaphase
(III) Sister chromatids get separated by splitting of Centromere – Anaphase II
(IV) Homologous chromosomes appear as bivalent or tetrad – Metaphase II
Answer:
(IV) Homologous chromosomes appear as bivalent or tetrad – Metaphase II
![]()
Question 2.
Most nëurons remain in G-’o’ stage do not divide
(I) This technique can be applied to replace neurons in dementia patients
(II) neurons can be activated by giving electric shocks
(III) neurons can be replaced by surgical procedures
(IV) Dead or injured neurons can be replaced by stem cell therapy
Answer:
(IV) Dead or injured neurons can be replaced by stem cell therapy
V.
Question 1.
Match the following and find the
(I) Robert Brown – A) Coined the word cell
(II) Robert Hook – B) Coined the word Mitosis
(III) Schleiden & Schwann – C) Studied the presence of Nucleus in cells
(IV) Waither Flemming – D) Cell theory
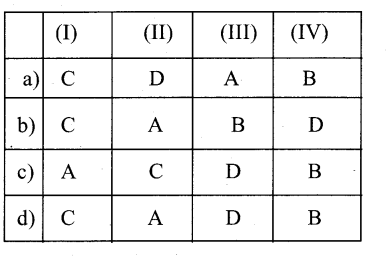
Answer:
d) C-A- D- B
![]()
Question 2.
(I) Cell cycle – A) division that follows the nuclear division
(II) Restriction point – B) Longest part but not resting stage
(III) lnterphae – C) A series of events leading to the formation of a new Cell
(IV) Cytokinesis – D) The checkpoint at the end of Gi determine a cell’s fate
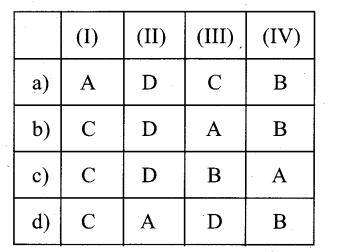
Answer:
c) C-D- B- A
VI.
Question 1.
Read the following Assertion and Reason. Find the correct answer
Assertion A: The mitochondrial inheritance in higher animals is uniparental
Reason R: The mitochondria from the male partner either undergo degeneration or rejected and only mitochondria from egg or ova is accepted.
(a) Assertion and Reason are correct Reason is explaining assertion
(b) Assertion and Reason are correct, but the reason is not explaining assertion
(c) Assertion is true but Reason not explaining assertion
(d) Assertion is true but Reason is wrong
Answer:
a) Assertion and Reason are correct. Reason is explaining assertion
![]()
Question 2.
Assertion A: In Meiosis Prophase I is a longer but significant phase
Reason R: Chiasma formation and crossing over takes place and recombination takes place
(a) Assertion and Reason are correct Reason is explaining Assertion
(b) Assertion and Reason are correct but Reason is not explaining Assertion
(c) Assertion is true but Reason is wrong
(d) Assertion is true but Reason not explaining Assertion
Answer:
b) Assertion and Reason are correct but Reason is not explaining Assertion
Question 3.
Assertion A: Interphase is the longest part of cell division and the cell actively involved protein synthesis & DNA synthesis
Reason: The Interphase is also known as the resting phase, & the cell takes rest between successive cell division
(a) Assertion and Reason are correct Reason is explaining Assertion
(b) Assertion and Reason are correct but Reason is not explaining Assertion
(c) Assertion is true but Reason is wrong
(d) Assertion is true but Reason not explaining assertion
Answer:
c) Assertion is true but Reason is wrong
![]()
Question 4.
Assertion A: The sister chromatids of homologous chromosomes exchange chromosomal bits
Reason R: This process of exchange of chromosomal bits is known as crossing over
(a) Assertion and Reason are correct Reason is explaining Assertion
(b) Assertion and Reason are correct but Reason is not explaining Assertion
(c) Assertion is true but Reason is wrong
(d) Assertion is true but Reason not explaining assertion
Answer:
d) Assertion is true but Reason not explaining assertion
VII.
Question 1.
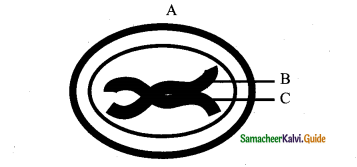
See the diagram & label the parts
Answer:
A – Leptotene
B – Chromosomes are visible under a light microscope
C – Paired sister chromatids begin to condense
![]()
Question 2.
See the diagram and write the correct answer.
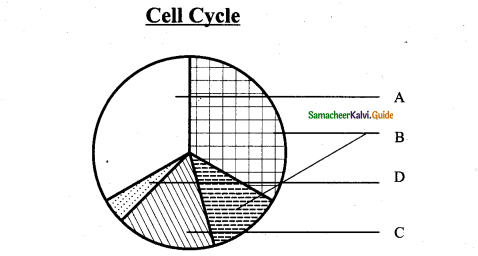
|
A |
B | C |
D |
| a) Cell growth | interphase | Mitotic phase | Cyto kinesis |
| b) Interphase | Cell growth | Mitotic phase | Cytokinesis |
| c) Cell growth | Inter Phase | Cytokinesis | Mitotic phase |
| d) Interphase | Cell growth | Cytokineses | Mitotic phase |
Answer:
a) Cell growth – Interphase – Mitotic phase – Cyto kinesis
Question 3.
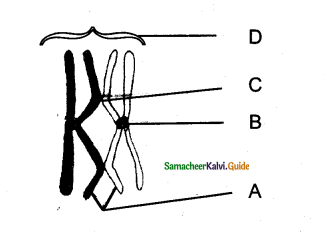
See the diagram & label Find out the correct labelling.
| A | B | C | D | |
| a) | Chromatin | Kineto chore | See constriction | Centromere |
| b) | Centromere | Chromatin | See constriction | Kineto chore |
| c) | Centromere | Kineto chore | Chromatin | Centomere |
| d) | Chromatin | See Constriction | Kineto chore | Centomere |
Answer:
b) Centromere – Chromatin – Secondary constriction – Kinetochore
![]()
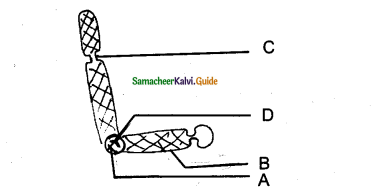
Question 4.
Label the diagram properly.
Answer:
A – Non-sister Chromatids
B – Centromere
C – Chiasma
D – Bivalent or Tetrad
Question 5.
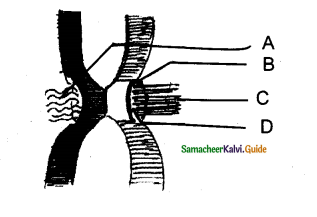
Answer:
A – Outer kinetochore
B – Fibrous corona
C – Inner Kinetochore
D – Microtubules
![]()
2 Mark Questions.
Question 1.
Name the two types of nuclear division.
Answer:
The two types of nuclear division:
- Mitosis and
- Meiosis.
Question 2.
What are the reasons for the arresting growth of cell during G1 Phase?
Answer:
- Deprivation of nutrition
- Lack of growth factors or density-dependent inhibition occur
- Some metabolic changes leads to Go – stage
![]()
Question 3.
Point out the reasons responsible for the arresting of the cell in the G1 phase?
Answer:
Cells are arrested in G1 due to:
- Nutrient deprivation
- Lack of growth factors or density dependant inhibition
- Undergo metabolic changes and enter into G0 state.
Question 4.
Differentiate between karyokinesis and Cytokinesis of Amitosis.
Answer:
|
Karyokinesis |
Cytokinesis |
| Division of Nucleus occur | Division of Cytoplasm occur |
| Nucleus develop contraction at the centre become dumbbell shaped contriction deepen divide nucleus into two | Plasma membrane develop constriction along with nuclear contraction, which deepen centripetally and the cell divides into two |
Question 5.
Define amitosis & write about its drawbacks.
Answer:
Amitosis is known as Direct cell division or Incipient cell division.
No spindle formation, no condensation of chromatin material occur.
It has one 2 steps
- Karyokinesis
- Cytokinesis
Drawbacks: Causes unequal distribution of chromosomes Can lead to abnormalities in
- metabolism
- reproduction
![]()
Question 6.
Distinguish between Closed and Open mitosis.
Answer:
|
Closed mitosis |
Open mitosis |
| Nuclear envelope remain intact & chromosomes migrate to opposite poles of a spindle with in the Nucleus Eg – Unicellular Eukaryotes – Yeast, Slime molds |
Nuclear envelope breaks down and then reforms around the 2 sets of separated Chromosome Eg – Most higher Plants & Animals |
Question 7.
Differentiate between Anastral and Amphiastral cell division
Answer:
|
Anastral |
Amphiastral |
|
|
Question 8.
What happens to plant cells at the end of Telophase in Mitosis?
Answer:
In plants, phragmoplast are formed between the daughter cells. A cell plate is formed between the two daughter cells, reconstruction of cell wall takes place. Finally, the cells are separated by the distribution of organelles, macromolecules into two newly formed daughter cells.
![]()
Question 9.
Differentiate meiosis in Plants & Animals.
Answer:
|
Plants |
Animals |
| In flowering plants meiosis occur during Microsporogenesis (anther) & in Mega sporogenesis (i.e) (ovule) development | It take place in reproductive organs at the time of production of gametes Spermatogenesis – produces haploid sperms Oogenesis – produces haploid eeas |
Question 10.
Define Mitogens.
Answer:
- The biochemical substances or factors which promote cell cycle acceleration & proliferation is called Mitogen.
- Eg. Gibberellin, Ethylene, Indole Acelic Acid, Kinetin.
- They are also known as Growth promotors.
![]()
Question 11.
Explain briefly about Endomitosis.
Answer:
The replication of chromosomes in the absence of nuclear division and cytoplasmic division resulting in numerous copies within each cell is called endomitosis. Chromonema do not separate to form chromosomes but remain closely associated with each other. Nuclear membrane does not rupture. So no spindle formation. It occurs notably in the salivary glands of Drosophila and other flies. Cells in these tissues contain giant chromosomes (polyteny), each consisting of over thousands of intimately associated, or synapsed, chromatids. Example: Polytene chromosome.
3 Mark Questions
Question 1.
Write down the significance of Meiosis.
Answer:
- Maintain chromosome number constant
- Crossing over (exchange of genetic meterial) leads to variations
- Variation – the raw material for Evolution
- Finally, meiosis produces genetic variability by partitioning different combinations of genes into gametes through an independent assortment.
- Responsible for Adaptations of organisms to various environmental stress.
![]()
Question 2.
Differentiate between Mitosis in Plants & Animals.
Answer:
|
Plants |
Animals |
| Centrioles are absent | Centrioles are present |
| Asters are not formed | Asters are formed |
| Cell division involves the formation of a cell | Cell division involves furrowing and cleavage of cytoplasm |
| Occurs mainly at the meristem | Occurs in tissues throughout the body |
Question 3.
Explain Endomitosis.
Answer:
Sometimes, the replication of chromosomes occur in the absence of karyokinesis & cytokinesis resulting in numerous copies within each cell condition known as Endomitosis.
- Chromonema donot separate to form Chromosomes
- Nuclear membrance does not repture
- No spindle formation occur
- Each chromosome consisting of over thousands of synapsed Chromatids
Eg – Salvary gland chromosome of Drosophila (Polytene or Chromosome).
![]()
Question 4.
Differentiate between Anaphase I & Anaphase II of Meiosis.
Answer:
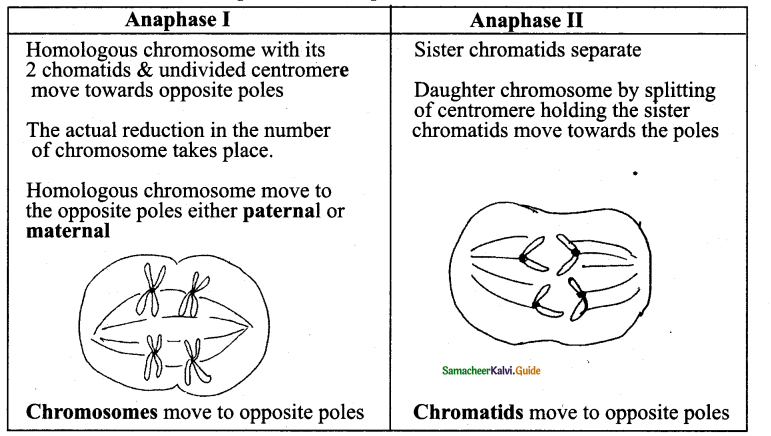
5 Mark Questions
Question 1.
Explain in detail the various stages of Prophase I.
Answer:
The various stages of Prophase I:
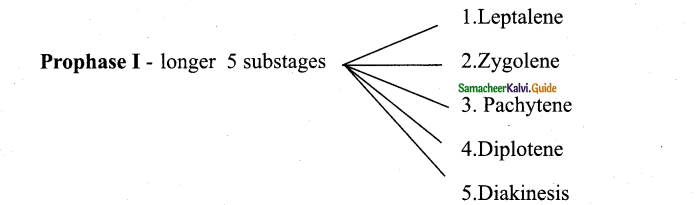
1. Prophase I – Prophase I is of longer duration and it is divided into 5 substages – Leptotene, Zygotene, Pachytene, Diplotene and Diakinesis.
2. Leptotene – Chromosomes are visible under light microscope. Condensation of chromosomes takes place. Paired sister chromatids begin to condense.
3. Zygotene – Pairing of homologous chromosomes takes place and it is known as synapsis. Chromosome synapsis is made by the formation of synaptonemal complex. The complex formed by the homologous chromosomes are called as bivalent (tetrads).
4. Pachytene – At this stage bivalent chromosomes are clearly visible as tetrads. Bivalent of meiosis I consists of 4 chromatids and 2 centromeres. Synapsis is completed and recombination nodules appear at a site where crossing over takes place between non – sister chromatids of homologous chromosome. Recombination of homologous chromosomes is completed by the end of the stage but the chromosomes are linked at the sites of crossing over. This is mediated by the enzyme recombinase.
5. Diplotene – Synaptonemal complex disassembled and dissolves. The homologous chromosomes remain attached at one or more points where crossing over has taken place. These points of attachment where ‘X’ shaped structures occur at the sites of crossing over is called.
6. Chiasmata: Chiasmata are chromatin structures at sites where recombination has been taken place. They are specialised chromosomal structures that hold the homologous chromosomes together. Sister chromatids remain closely associated whereas the homologous chromosomes tend to separate from each other but are held together by chiasmata. This substage may last for days or years depending on the sex and organism. The chromosomes are very actively transcribed in females as the egg stores up materials for use during embryonic development. In animals, the chromosomes have prominent loops called lampbrush chromosome.
7. Diakinesis – Terminalisation of chiasmata. Spindle fibres assemble. Nuclear envelope breaks down. Homologous chromosomes become short and condensed. Nucleolus disappears.
![]()
Question 2.
Explain karyokinesis in mitosis of plant cell
Answer:

Prophase – Longest Phase
- Chromosomes visible thread like condenses into thick chromosomes
- Initiation of spindle fibres occur
- Nucleolus disappear Nuclear envelope breaks down
- Golgi apparatus & ER not seen
Metaphase
- Sister chromatids attached to spindle fibres by kinetochore of centromere
- Chromosome align on the equatorial plane (metaphase plate)
(spindle assembly check point decide the fate of the cell)
Anaphase
- Centromere split daughter chromatids move to opposite poles
- Shortening of spindle create pull divide centromere & divide chromosome into a chromatids
(APC /C leads to degradation of protein lead to separation of chromatids
Telophase
- Genetic material division completed Nucleolus & Nuclear membrane reform.
- Sister chromatids become thick chromosomes with its own centromere.
![]()
Question 3.
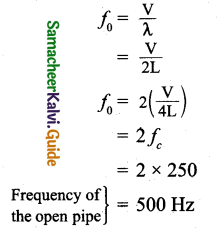
Explain S phase & G2 phase, til S Phase
Answer:
(i) S Phase:
- Known as synthetic phase of interphase of mitosis
- Growth of cell continues
- Replication of DNA occur
- Histones synthesised and attach to DNA
- Duplication of centrioles occur
- DNA content doubles from 2C to 4C
(ii) G2 phase
- 4 C amount of DNA
- Cell growth continues
- Synthesis of
- organelle,
- mitochondria & chloroplast
- tubulin synthesised, microtubules formed
- Spindle begin to occur
- Nuclear division follows
- MPF (Maturation Promoting factor) formed brings out condensation of interphase chromosomes into mitotic form.
![]()
Question 4.
Draw the Cell cycle.
Answer:
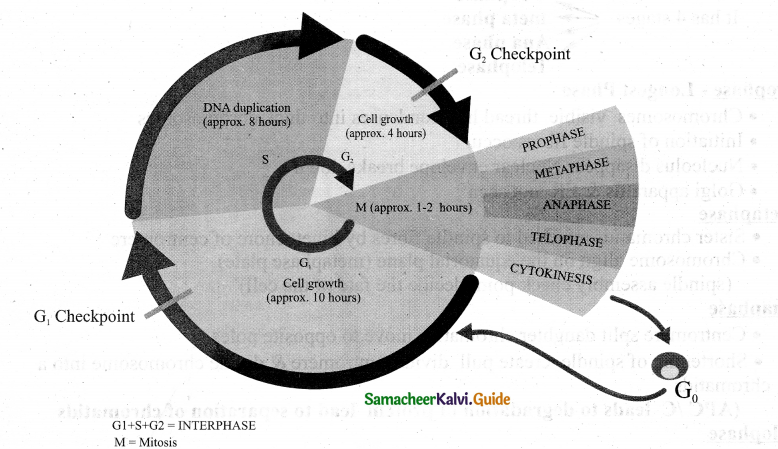
Question 5.
What are the significances of Mitosis.
Answer:
Exact copy of the parent cell is produced by mitosis (genetically identical).
- Genetic stability – Daughter cells are genetically identical to parent cells.
- Growth – As multicellular organisms grow, the number of cells making up their tissue increases. The new cells must be identical to the existing ones.
- Repair of tissues – Damaged cells must be replaced by identical new cells by mitosis.
- Asexual reproduction – Asexual reproduction results in offspring that are identical to the parent. Example Yeast and Amoeba.
- In flowering plants, structure such as bulbs, corms, tubers, rhizomes and runners are produced by mitotic division. When they separate from the parent, they form a new individual. The production of large numbers of offsprings in a short period of time, is possible only by mitosis. In genetic engineering and biotechnology, tissues are grown by mitosis (i.e. in tissue culture).
- Regeneration – Arms of starfish
![]()